Category: information security
NSA intell goldmine, who else has access?
<also on HuffPo UK>
 Shortly after the initial release of some documents from whistleblower Edward Snowden I wrote a little summary about the IT-policy implications for Europe based on earlier columns. A lot of additional documents have come out since then and we can basically conclude that almost every computer system on the planet is fully broken or at least very vulnerable to NSA interference or manipulation.
Shortly after the initial release of some documents from whistleblower Edward Snowden I wrote a little summary about the IT-policy implications for Europe based on earlier columns. A lot of additional documents have come out since then and we can basically conclude that almost every computer system on the planet is fully broken or at least very vulnerable to NSA interference or manipulation.
Nobody, including the NSA, Edward Snowden, Glenn Greenwald has a total oversight of all the in the tens of thousands of documents let alone the political or strategic implications of the info contained in them. Most of the news keeps focusing on the ‘scandal’ aspect and/or the person of Snowden. Being angry at the US government (practised by most opponents) and attacking the person of Snowden (a favorite of apologists of the US regime) distracts from defining adequate policy responses and so far there have been precisely none in Europe. This constitutes a massive failure of the various EU governments to protect their citizens’ rights and the economic sovereignty of their nations. It is also strange in light of the fact that an adequate policy response had already been formulated in July 2001 and really just needs to be implemented.
But every now and them the disinfo spread by some apologists for the behaviors of the NSA is useful for understanding how much worse the situation may just turn out to be. This article by a former NSA employee is a nice example of an attempt at smearing the whistleblower while actually digging the hole the NSA (and the US regime) is in much, much deeper. The piece claims Snowden secretly worked for Russian intelligence all along. While I do not share the authors views on Snowden’s motivations or allegiances the suggestion that outside organisations could have agents inside the NSA has some interesting implications.
If I understand the gist of this post correctly there is a much bigger breach than one would conclude based on the mainstream news from the Guardian. Not only can (and does) the NSA collect pretty much everything anyone does in the digital realm by breaking systems and breaking into systems. They then are unable to protect this sigint goldmine from falling into the hands the agents of foreign intelligence organisations. So now all our data is in the hands of both the US and Russian governments. This begs the question what other organisations have deep-cover moles inside the NSA using its infrastructure to do the hard works of global sigint for them? The Chinese government? A South-American drugs Cartel? Private Military Companies? Journalists-activist-terrorists? Goldman Sachs? The implications are astounding.
If what this academic-with-the-columnist-style says it true the disaster is exponentially much bigger than it would initially appear to be and this has very little to do with any ‘damage’ to the US image (it’s got nowhere to go but up by now) or its ability to ‘do’ intelligence. First America gave the world the Internet as a global comms infrastructure and now it has given an unknown number of completely unaccountable actors the keys to this infrastructure to do with as they please.
A Russian/Chinese/Israeli/Iranian spy will benefit both from the sigint collected by the NSA systems and even more from the info about what the US Intelligence community is (and is not) looking at. They could maybe also manipulate the collection process to steer the NSA away from things they would like to remain unseen. Any serious spy organisation would spend a lot of resources on creating that ability since the US has made itself totally dependent on signals intelligence as opposed to humans in the field who speak languages and understand cultures.
If the NSA has created a global spying machine whose output they cannot control perhaps it would be best to shut the whole thing down today. This would also have the additional benefit of respecting the human right of privacy (as described in Article 12 of the universal declaration of human rights) for most of humanity.
Privacy, a decade on
<originally a column for Webwereld – in Dutch>
On July 11th 2001 the European Parliament published a report on the Echelon spy network and the implications for European citizens and businesses. Speculations about the existence of this network of Great Britain-and-her-former-colonies had been going on for years but it took until 1999 for a journalist to publish a report that moved the subject out of the tinfoil-hat- zone. The report of the EU Parliament contains very practical and sensible proposals, but because of events two months after publication, they have never been implemented. Or even discussed further.
Under the heading "Measures to encourage self-protection by citizens and enterprises" lists several concrete proposals for inproving data security and confidentiality of communications for EU citizens. The document calls on Parliament to inform citizens about the existence of Echelon and the implications for their privacy. This information must be "accompanied by practical assistance in designing and implementing comprehensive protection measures, including the security of information technology". So not just some abstract government infomercial on TV/radio but hands-on tips to get some actual work done please!
Appropriate measures
Other gems are the requests to "take appropriate measures to promote, develop and manufacture European encryption technology and software and, above all, to support projects aimed at developing user encryption technology, which are open-source" and "promote software projects whose source text is published, thereby guaranteeing that the software has no "back doors" built in (the so-called "open source software") ". The document also mentions explicitly the unreliability of security and encryption technologies whose source code is not published. This is an issue that is a strict taboo in Dutch and UK discussions on IT strategy for governments (probably because some major NATO partners might be offended).
Also, governments must set a good example to each other and their citizens by "systematic use of encryption of e-mails, so that in the longer term this will be normal practice." This should in practice be realised by "ensuring the training and publication of their staff with new encryption technologies and techniques by means of the necessary practical training and courses." Even candidate countries of the EU should be helped "if they cannot provide the necessary protection by a lack of technological independence". Unfortunately to this day I cannot send encrypted mails to officials and the vast majority of them do not even digitally sign their emails to allow me to verify the integrity of the content. Despite the fact the software that makes this possible has been available as open source since before publication of the report in 2001.
That one paragraph from the summer of 2001, when rational security policies had not yet been destroyed by September 11th, decribes the basis for a solid IT policy that ensures security and privacy of citizens against threats from both foreign actors and the government itself.
What a difference a decade makes …
Last Monday Privacy First organised a lecture & discussion evening on cyber security and the relationship with terrorism. Will van Gemert, director of National Cyber ??Security for the Coordinator for Counterterrorism and Security gave a lecture on the relationship between privacy and security. In this lecture there was much talk about consumers, little about people/citizens (perhaps the difference is a bit foggy from the windows of government skyscrapers in The Hague). He also insisted that the Government is very much working with ‘the market’ and private parties. It was probably meant to be reassuring but had the opposite effect on most attendees. Ideas from the EU document mentioned above, such as better IT education, open source encryption and technological diversity as defensive tactics, were unfortunately completely unknown concepts. The ribbon on the doors of the Cyber ??Security section of the National Counter Terrorism organisation had just been cut ,so perhaps things will be better in a year. We can but hope*.
A few weeks earlier, another of our government speakers defending even more colourfully the Clean IT project at a meeting of RIPE (the organization that distributes IP addresses for Europe and Asia). Clean-IT is a European project of Dutch origin which aims to combat the use of the Internet for terrorist purposes.
Terrorism is not defined
The problem with this goal is that ‘internet’, ‘use’ and ‘terrorism’ remain undefined, nor is anyone very interested in sorting this out. This in itself can useful if you are a government because you can then take a project in any direction you like. A bit like when data retention was rammed through the EU parliament in 2005 with the promise that it would be used only against "terrorism" – a promise that within a few months was broken. In Germany, data retention has now been declared unconstitutional and been abolished, while in the Netherlands we have rampant tapping, despite a total lack of evidence of the effectiveness of these measures. That all the databases of retained telecommunications data themselves become a target is not something that seems to be seriously taken into account in the threat analyses. All rather worriying for a government that is still usually unable to secure its own systems properly or ensure that hired private parties do so.
Also, during the lecture on Clean-IT much emphasis was placed on the public-private partnership to reassure the audience, yet this had a predominantly opposite effect. It’s strange that a government first proves itself incompetent by outsourcing all expertise, then it comes back after ten years and claims it cannot control those same comapnies, nor indeed their sub-contractors. The last step is then to outsource to companies that used as reassurance to citizens commented: "We let by companies do it! That you as a citizen do not think that we ourselves with our sausage fingers sit! Come all good". After Diginotar my confidence in the guiding and supervisory capacity of the government has dropped to just above absolute zero.
What a difference in approach between the summer of 2001 and today.
Terrorism is obviously the "access all areas pass" – but many more Europeans die slipping in the shower or from ill-fitting moped helmets than from "terrorism". Moreover, we as Europeans have experience of dealing with terrorism. ETA, IRA and RAF were rendered harmless in previous decades by police investigations, negotiations and encapsulation. This was done without jeopardizing the civic rights of half a billion European citizens. Even when weekly IRA bombs exploded in London nobody suggested dropping white phosphorous on Dublin or Belfast.
Hope
I hope* that the pre-9/11 vision of the EU Parliament will finally penetrate the Dutch Ministry of Security and Justice (formerly just ‘Justice’ soon ‘Love‘?). Perhaps a new cabinet will lead to new initiatives and opportunities? It would be nice if the ‘free West’ could develop a policy that would justify our moral superiority towards Russia, when we demand that they stop political censorship under the guise of "security".
* Hope: the desire for a future situation over which you have little or no influence: "I hope my plane does not crash."
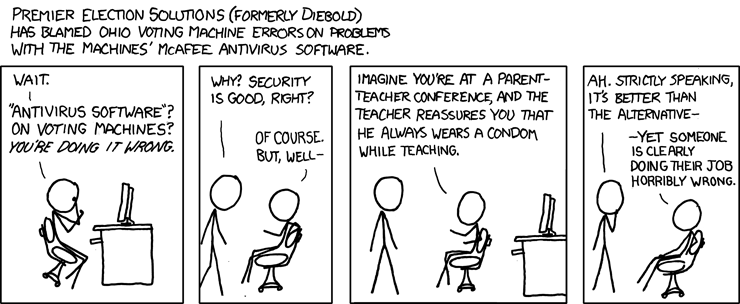
Votingcomputer: the zombie that just won’t die
<originally a Webwereld column>
Last month the VVD and D66 political parties (the Dutch equivalent of the Conservatives and LibDems in the UK) again proposed that the Netherlands should re-adopt electronic voting. Earlier this year the Dutch Association of Mayors also called for their reintroduction (don’t you just love it when non-elected officials comment on and interfere with the electoral process :-). While the use of voting computers in the Netherlands has been banned for over four years, even for water board elections, there remains a fundamental misunderstanding of the basic problem with electronic voting.
While the many clumsy security problems (video) or the absence of the source code of the software (in the case of Nedap and SDU voting computers), are excellent talking points for the media and political agenda, these issues are not the core of the problem. And although the voting computer dossier at the Ministry of Home Affairs is now labelled with a bright fluorescent sticker: ‘radioactive, do not touch!", there is still a risk that local authorities or suppliers will continue to feel that voting by computer is best "if we can just iron out a few little bugs”.
The real objections are more fundamental and have little to do with security bugs or open source code. They are the fundamental principles underpinning our democracy, and are threatened by the use of voting computers. In the many discussions on mailing lists and web forums it seems that people have lost sight of these principles.
In the first year of operations of the wedonttrustvotingcomputers work group, there were many reassurances given by government and suppliers that we should not be so suspicious. The Netherlands is a great country, after all, and the suggestion that anyone would commit fraud with something so fundamental as the election was considered ridiculous. It was simply unthinkable, and further discussion or justification not considered necessary. This attitude demonstrates a fundamental misunderstanding of the essence of democracy. That is not a question of trust but distrust of organised power.
Through trial and error we have learned over the past few thousand years that power corrupts, and absolute power can corrupt absolutely. An enlightened dictator can be an efficient form of government, but how do you ensure they remain enlightened once they have the power? To solve this problem we have evolved a complex system of temporary mandate (four years), with checks and balances as the need arises. You can only gain power if the majority of people have said that they really want you there, and even then you will be closely monitored by 150 other people who are also only be allowed to do so because of the vote of thousands of fellow citizens. The system is far from perfect and is plagued by inertia and a focus on what is hot in the media, but we have yet to invent something better. This system makes it difficult to take important decisions publicly without authorisation. And a king or president cannot simply on a whim ruin the country or violate the fundamental rights of citizens – unless those citizens and their representatives agree to it by inaction, but then they only have themselves to blame.
The abuse of power cannot be solved by online publication of a voting computer’s source code because citizens cannot determine whether the published source code actually runs on the specific voting computers in their neighborhood. Even more important is the fact that 99.99% of the population cannot audit the code. Inevitably, it still comes down to having confidence in a very small group of technical experts. And having to trust a very small group (any small group whatsoever!) is precisely what we no longer want. If we have small groups of technicians whom we trust, we might as well make up the parliament based on a sample of a research firm. That saves a lot of time and paper and there is probably a great evening of TV programs that can be built around it.
It has often been said that paper ballots can also be fraudulent, with elections in places like Zimbabwe cited as examples. The important aspect here is not the possibility of fraud but the possibility of detection when it happens. Large-scale, and therefore effective, fraud in a paper voting system is impossible to keep secret and that makes it possible to intervene when small groups try to exploit the system. In most cases, fraud with voting computers is impossible to prove afterwards. The records are erased and there are no ballot papers available for another recount.
This was proven painfully during a local election where the candidate eldermen was also the operator of the voting computer. In the polling station where he was present he received an unlikely number of votes (higher than all other locations in the municipality combined). Yet the justice department was hard pressed to find actual evidence against this potential fraudster. Nor could the man ever prove his innocence. The result is therefore a situation where the integrity of the process itself is called into question, and thus the legitimacy of the ballot. The distinction is thus the detectability of fraud, not the (im)possibility of it.
Even with electronic voting with a printed ballot (the so-called ‘paper trail‘) there can be doubts about the results, and applications for a recount of a paper trail is also an immediate political issue (against winners, losers). At what point do we initiate a paper recount? Which sample is good enough for the loser? How do we determine that there is reason to doubt the electronic result? Is there a basic assumption that the computer counts accurately? So there are inevitable administrative and political barriers to requesting a recount. This, combined with the fact that polling can provide the perception of a "winning" coalition in the Netherlands, makes it attractive to manipulate voting computers. What is it worth to control the election of the 20th largest economy on the planet?
Despite minor incidents with the paper system, the integrity of the Dutch paper voting process has never been the subject of discussion. And even the Interior Ministry and TNO had to admit, after some urging from external experts, that the previous generation of voting computers was not compatible (nor had it ever been compatible) with the Dutch electoral law.
TNO hid the fact that the validation protocol of the integrity of the system had not been examined. Both the responsible officials and TNO’s "experts" were simply not competent to deal with this issue adequately. The OV-chip, EPD and the Diginotar dramas were repetitions of this incompetence, displaying no understanding, no adequate assessment frameworks, and no substantive oversight. And , of course, nobody is held responsible when things go wrong. After voting machines were banned, no civil servants and TNO employees were sacked for their screw up. Therefore there is very little confidence amongst external experts that future assesments on a different technical ‘Solution’ will be adequate.
We must prevent a situation where the integrity of the electoral process itself can be questioned, and thus the legitimacy of the outcome. The vital distinction is the ability to detect fraud, not the (im)possibility thereof. Voting computers create serious problems, are more expensive that the use of paper, and undermine the legitimacy of democratic governments. And as Churchill said: ‘Democracy is the worst form of government, except for all those other forms that have been tried from time to time.’
(this column is a re-write from a 2008 publication I wrote for a Dutch magazine on digital government – now disapeared after site redesign)
Parliamentary hearing on IT-projects, security & privacy
On June 1st 2012 the Dutch government’s Parliamentary working group on government IT-projects held a hearing of experts. My written contribution below. Capture of videostream… (in Dutch). Dutch journalist Brenno de Winter published his thoughts here. Column on this published the week after here.
Introduction – IT and the Dutch national government
 Universality is an assumption of astrophysics that states that all phenomena, everywhere, behave as we observe them from Earth. I’m assuming that phenomena I have observed in specific government IT projects also occur in government IT projects that I have less infromation about (this is usually caused by the poor implementation of Freedom Of Information Acts, see the notes of Mr de Winter).
Universality is an assumption of astrophysics that states that all phenomena, everywhere, behave as we observe them from Earth. I’m assuming that phenomena I have observed in specific government IT projects also occur in government IT projects that I have less infromation about (this is usually caused by the poor implementation of Freedom Of Information Acts, see the notes of Mr de Winter).
IT project management is currently based on a rather naive model of reality – "smart entrepreneurs compete on a level playing field for the favours of the government, which then procures with insight and vision." However, this model does not adequately predict the observed outcome of the projects. Whence this group.
Another model would be "a corrupt swamp with the wrong incentives, populated by sharks and incompetent clowns". This model has the advantage of perfectly predicting the observed outcomes.
The price of outsourcing everything
No vision, no vigour, no knowledge, and especially no ambition to do anything to improve on any of these. This is the overarching theme of all government IT projects I have experienced both on the inside and externally. And I believe is the fundamental cause of the vast majority of practical problems the group wishes to understand.
From Knowledgenet to the National EHR, the Whale project, voting computers, the public transport card, and the failed attempt to break the monopoly of large software vendors – NOiV … the knee-jerk response remains the same: to reduce a social problem to a technical project that can then be quickly outsourced to IT suppliers and/or advisors. The societal aspects are quickly lost once the train of political promises, commercial interests and project logic leaves the station and becomes unstoppable. Even the parliamentary group on IT projects aims to outsource part of its work to an external company. The chances are that the selected external company will already have as its main selling-point an umbrella contract with the national government. Probably this company will already have been advisors on one or more of the projects that may be under investigation.
In my experience as an advisor of a large government project (from the list of projects provided by the work group), I had to advise another consultant on how to hire yet other outside consultants to perform a security audit. The argument that the government has difficulty in hiring and retaining specialised expertise may be true in specific cases, but in reality, most of the hired ”IT workers” have no specialist expertise. Often they are generalists and/or project managers without much substantive technical knowledge. The inability of government to attract competent personnel should be seen as a problem that needs to be solved and not as an immutable law of nature. If we truly want something to change, we really need to be willing to change anything/everything.
Focus of the research proposal: look at the forest, not at the trees
By focusing on individual projects it is likely that the working group will only look at operational issues within these projects. The broader, underlying causes remain hidden, yet that is precisely where many failures begin. Moreover, it is especially important to look at such overarching issues as potential factors in future projects.
If anything has become clear since the Diginotar case, it is the total lack of accountability or sanctions subsequent to the failure of both executive and supervisory organisations and officials. Suppliers and officials who have endangered the security of citizens and the functioning of the state have largely remained in position, free to repeat their mistakes in a few more years. Evaluation, in this context, is therefore only useful if lessons learned from them can be used to prevent a repetition of similar birth defects in new projects in the future.
Analyse context: causes and societal consequences of failure
When the EHR project was cancelled by the Senate, there was great indignation about the "wasted" 300 million Euros that had been spent. In my view, the 300 million is not the issue we should be focusing on. If the figures used by the Health Ministry and Nictiz concerning the need for the EHR system were correct, the real costs of the failure of the EHR system over the past 12 years are more than 20,000 lives and 16 billion Euros.
Therefore the real question is why Nictiz on the one hand did not have either the budget or the required mandate to deal with the problem, and on the other hand why this national disaster was not the most important issue for the Health Ministry to address. Why did the leadership of the Ministry not have its hand on the wheel, with weekly reports to the Cabinet and parliament?
If the publicly-stated figures are incorrect, Parliament has been misinformed for more than 12 years and the project should never have been started. Either way, something went very wrong and it had very little to do with the technical aspects of the project (although there was enough to criticise there as well).
The above example is just one of many cases where the formal administrative motivation for a project and subsequently allocated funds and mandates bear no logical relationship.
Also the projects concerning the introduction of voting computers and the public transport card, had logical holes of Alice-in-Wonderland-like proportions. A very high level of public transparency about new projects here would probably have enabled citizens to provide both solicited and unsolicited assistance to the government in finding these holes.
It would also help to restore some confidence amongst citizens, whose faith has been repeatedly dented. On the one hand the government uses its own incompetence as an excuse for failure, while on the other hand two weeks later it will ask its citizens to rely on its ability to finish a new megalomaniac techno-fix for a complex social issue. The current deep lack of credibility ultimately becomes a question of legitimacy.
Selection criteria for examining IT projects:
- Extent to which the original official motivations and assumptions were not investigated or found not to be substantiated. What was the problem? How would the proposed IT project fix this? Why was the gap between policy and reality not foreseen?
- Social costs of not solving a problem (by the failure of the project); these are often multiples of the cost of the IT project itself.
- Damage to citizens and their rights because of the failure of project or because of incorrect technical and organisational choices made during implementation.
IT projects the working group hould include in the investigation:
- The EHR
- The public transport card
- The NOiV & the NCA investigation into the failure of this policy.
- GOLD / DWR – introduction of the ‘standardised’ workplace for the national government between 2004 and today.
Doublethink, Waiting for the Big One, Doctor doctor, Asbestos, Gran knows why, (my columns)
My Court of Audit questions for investigation into national openstandards and opensource policy 2010
Prof. Eben Moglen explains the big societal picture (45 min speech) – must watch!
Waiting for the big one
<originally a Webwereld column – in Dutch>
 Diginotar’s multiple IT failures in the public sector have been swept under the carpet. So far, nothing indicates that there will be any real change to the Dutch government’s overdue IT projects. During the hearing (mp3 – in Dutch) in the Lower House it was apparent that neither the government overseer OPTA or auditor Price Waterhouse Coopers believe themselves at fault, despite the fact that for years as regulators they have rubber stamped the work of Diginotar. The decisions of the PwC auditors were obviously good because "they are executed by responsible professionals". This will be heartening for all those Iranian citizens who are suffering the consequences of this (think of an unpleasant convergence of kneecaps and power tools).
Diginotar’s multiple IT failures in the public sector have been swept under the carpet. So far, nothing indicates that there will be any real change to the Dutch government’s overdue IT projects. During the hearing (mp3 – in Dutch) in the Lower House it was apparent that neither the government overseer OPTA or auditor Price Waterhouse Coopers believe themselves at fault, despite the fact that for years as regulators they have rubber stamped the work of Diginotar. The decisions of the PwC auditors were obviously good because "they are executed by responsible professionals". This will be heartening for all those Iranian citizens who are suffering the consequences of this (think of an unpleasant convergence of kneecaps and power tools).
But because of the chaos at Diginotar, we may never know for certain the full horror of those consequences. It is very simple for someone to take over an entire network and manipulate all the logs. The only thing we can really say with any certainty is that so far we have no reason to believe that IT security was any better in the past than the recently discovered FoxIT mess. The PwC audits are obviously not able to detect such a mess and OPTA apparently did not even look. Possibly Diginotar has been totally hacked for many years, and nobody noticed. A really smart spy or cyber criminal does his job and leaves no traces. The many detailed discussions about the exact scale and timeline of the hack have completely ignored this fact. From his grave Socrates is smiling at the idea that we only certainly know what we certainly do not know.
The most important question is surely: "how can we prevent such a critical part of our IT infrastructure from falling into foreign hands?". But this question was apparently not even on the radar of our regulators or MPs. Recent discussions about the USA browsing through our systems without judicial oversight make this question particularly pertinent. But perhaps I am somewhat naive to expect that my government to be both capable and motivated to protect the interests of its citizens.
Teamwork: it spreads the blame
Diginotar is yet another egregious example of a public IT function going terribly wrong at every conceivable level (selection, implementation, monitoring), and yet nobody being held responsible for the consequences. It is important to recognise that we shall probably never know how serious the real consequences were – especially for that unknown number of Iranian citizens. As a direct result, we must also recognise that we need to replace the people who did this “monitoring”and the "methods" they used. To continue to do the same and yet expect different results is one of the definitions of insanity.
Know nothing, do nothing
If a key IT organisation appointed by the government fails, it is down to a lack of crucial expertise in the government. Everything is privatized and the resulting lack of expertise is an unfortunate consequence of a principle of degraded policy-making. Instead of identifying and solving this lack of substantive expertise, it is dismissed as an immutable law of nature. "It just is" that the government has no employees who have relevant expertise to evaluate, manage and oversee IT projects (or evaluate and oversee the hired vendors). Simultaneously, our citizens trust that same government to properly assess the feasibility and implications of increasingly megalomaniacal IT projects – another symptom of institutional madness.
I therefore see the debate about any special protection for hackers as whistleblowers, however well intentioned, as only a symptom. The government needs to “own” the information, at least to have the right to ask questions and to independently evaluate the answers to these questions. Or should we simply give away control of our sea dykes and hope that a few public-spirited people will report the hole in a dyke on their Sunday off?
Nothing can be leaked that could change the way the people in The Hague deal with these problems. Nobody loses their head, even after such a mega-failure as Diginotar: and in comparison the implementation of both the electronic medical records and the public transport Chipcard pales into insignificance, butno doubt these projects also continue despite faillure after faillure.
What is necessary for a real breakthrough? Like I said in a debate about the EMR in 2005: an event that is too terrible to ignore. Because that is always what it takes in the Netherlands to shift our political-administrative system down a different path. It is always susceptible to the pressures of existing commercial interests or the idea of a couple of people losing their jobs. The complexity of Dutch society and the economy might itself bring about that change: something like a national breakdown of hospital systems, or something like an exploding refinery in the Rotterdam area. There are so many vulnerabilites to choose from.
I suspect there is a “sweet spot” in terms of deaths versus effective political impact. Somewhere between the Enschede fireworks disaster (23 dead) and the 1953 flood (1835 dead), so to speak. I share Rop Gongrijp’s analysis that after Diginotar nothing will change (because there were no deaths on TV). We are waiting for the big blow that is strong enough to make real change possible. Only then will there room for other people with more technical expertise, involving a much higher level of technical requirements and transparency of all the inter-related processes such as design, selection and implementation of new systems.
Perhaps a cruel cyber attack with cute little piglets?

 Nederlands
Nederlands
 English
English